Spam & Virus Protection
Here's how the system works:
Steps 1 through 5 checks for known spammers and does an in-depth virus
check.
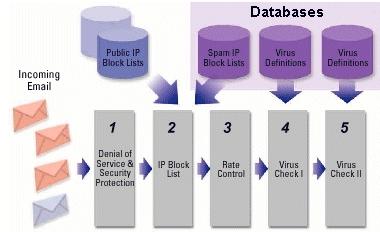
- Denial of Service and Security Protection. Mail comes in the
gateway. The rate and number of emails from a single source are
checked. The gateway protects against Denial of service attacks.
A Denial of Service or DOS attack is where a massive amount of remote
connections are made to a server, gateway or other device in a deliberate
attempt to overload the device and render it off line. It also
acts as a firewall to prevent unfriendly activity such as port probing.
- IP address black lists. The IP that the mail was sent from
is checked by two databases to see if it is from a known spammer.
- Rate control. This limits the speed in which any user
can send email to any one domain. This feature is needed to help guard
against (DHA) Directory Harvest Attack. This type of attack involves
the spammer sending thousands of emails in a few seconds to one domain.
The mail addresses that are being sent to are software generated. The
ones that bounce are determined to be no good while the ones that don't
bound are assumed to be good addresses. This is one trick spammers use
to get valid email addresses.
- Virus check I. The email passed through the first stage
of a virus check.
- Virus check II. The email is run through a more intense
virus check.
Steps 6 through 10 checks User rules then does intense spam checks.
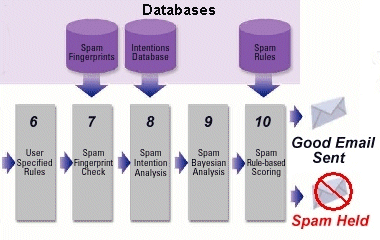
- User Specified Rules. The system then looks to see if (you)
the recipient has the sender in your white list as someone you want
to get email from. If the answer is yes no further checking of
the email is done and it is placed in your mailbox. If the answer
is NO then the email is passed to the spam filtering.
- Spam fingerprint check. The email is checked against
the spam fingerprint database to see if it finds a match to known spam
email.
- Spam Intention check. Here the email is checked to see
if it has known spam links or other identifying marks. This analysis
catches many of the emails that look legitimate but are still Intended
to be spam.
- Bayesian Analysis. The email passes to the Bayesian analysis
system. This takes an in depth look at the email to further determine
if it is spam.
- Based on the findings of all three spam databases the email
receives a score on the probability that it is spam. If the score
is high enough the email is marked as spam and not sent to the users
Inbox. Instead the email is held. With business email a system can't
simply throw away email that it thinks is spam. No system can be 100%
accurate 100% of the time. Each day the user is sent an email showing
them what has been held. The email contains a link the user can click
on to login. They can release or white list any email that they want
that has been held as spam. White listing the email means that the email
will not be held again. The user can also clean out all the spam that
was held. Altogether it's the best thing out there for catching viruses
and spam in one shot.
Spammers come up with new tricks each day. The system databases are updated
several times per week to keep up with the latest spammer tricks.
You will instantly see spam fall by over 85% as soon as you use this
system. The more you use it the better it gets at detecting spam.
Held mail called Quarantined mail is left on the system. You will receive
an email that an account was created automatically. The Anti-Spam system
will create a password for your account and it is sent with the email.
You can click a link in the email to login. You can change the password
once logged in under Preferences.
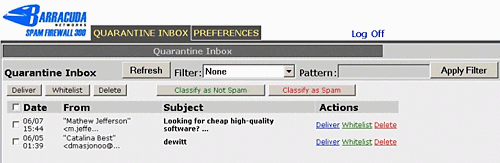
Email that is held in your Quarantine Inbox is shown in the example below.
The system learns what you consider to be spam by you selecting whether
each email held is spam or not. If somebody you really want mail from
has been caught you can put them in your Whitelist and they won't be caught
again unless you remove them from your Whitelist.
[ Back to Top ]
|



